Estimated reading time:3 minutes

99% of IT professionals see encrypted traffic as a possible source of security threats. Don’t let the encrypted traffic turn into security risk. Gain a scalable visibility of threats in encrypted traffic when preserving privacy and with no impediment to latency.
Encrypted Traffic Analysis is a method of malware detection and cryptographic assessment of secured network sessions, which does not rely on decryption.
This improves visibility of encrypted traffic while remaining scalable and causing no impediment to latency nor violation of privacy. While the number of malware campaigns hiding in encrypted traffic grows massively, ability to detect malicious SSL traffic becomes crucial for ensuring compliance and demanded level of protection.
The Flowmon solution addresses this need and offers the necessary insight while remaining scalable, easily integrable and, most importantly, respectful of privacy.
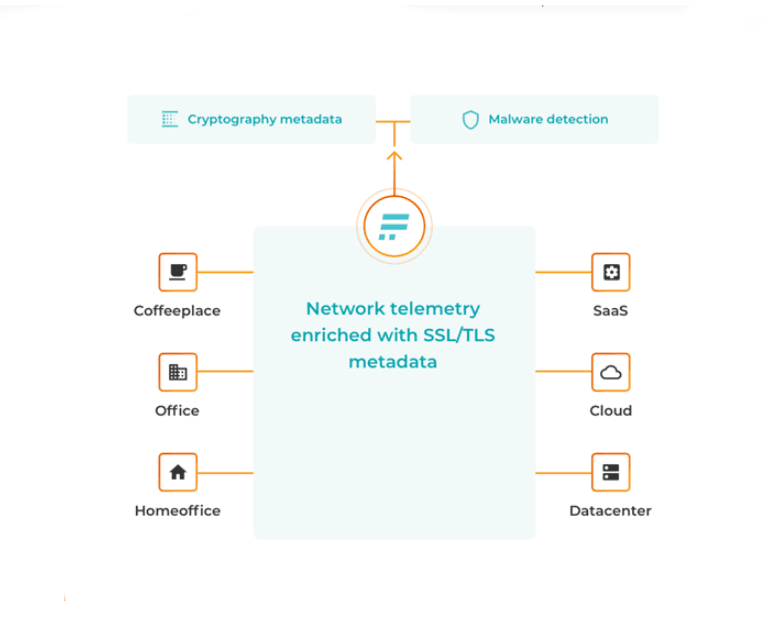
How Encrypted Traffic Analysis Works?
Flowmon Encrypted Traffic Analysis collects network traffic metadata in IPFIX format using passive probes and enriches it with TLS protocol information (among others). These attributes of the encrypted session between clients and servers are available regardless of the client’s physical location or whether the server runs in the cloud or datacenter.
This provides a wealth of insight about the traffic and allows for the identification of out-of-date SSL certificates, policy non-compliant certificates, encryption strength and old TLS versions that may contain faults or vulnerabilities. Furthermore, a machine learning engine uses this data to perform behavior analysis and anomaly detection to identify malware and other threats.
This approach does not violate privacy, nor does it degrade performance. It provides insightful analytics regardless of the volume. Moreover, since the data is stored in an aggregated form, it saves a considerable amount of storage space without impeding information fidelity.
Features
- Privacy preserving: Using network traffic metadata does not require decryption and causes no privacy compromise.
- Zero latancy impact: ETA is unobtrusive to the network. It provides monitoring with no impediment to operation.
- Heterogeneous Environments: On-premise, remote, hybrid or cloud makes no difference. It provides the same insights.
- Reduce response time: Provide an overview of all relevant events and detections without any clutter or information noise..
Resolve Compliance and Security Challenges
Monitor Compliance
- Expired and non-compliant SSL certificates to show which applications need an update
- Encryption strength by monitoring key length and algorithm
- Unwanted TLS versions that contain vulnerabilities
- Non-compliant clients accessing unwanted sites discovered by server name identification
Detect Cyberthreats
- Malware-infected stations diagnosed byanomalies in SSL parameters
- Malware C&C center communication revealed by JA3 fingerprinting
- Man-in-the-middle attacks manifested by unusual or illegitimate certificates
- Suspicious packet size indicating data exfiltration
Security Use Case Example: JA3 Fingerprinting
JA3 fingerprinting is an effective way of detecting malicious threats or at least to spot an indicator of compromise (IoC). This method combines these five parameters of TLS communication: version, ciphers, extensions, elliptic curves and its formats and produces a MD5 hash. This is our JA3 fingerprint. Interestingly, this is enough to identify various clients. For example, “e7d705a3286e19ea42f587b344ee6865” is the JA3 fingerprint for a standard TOR client.
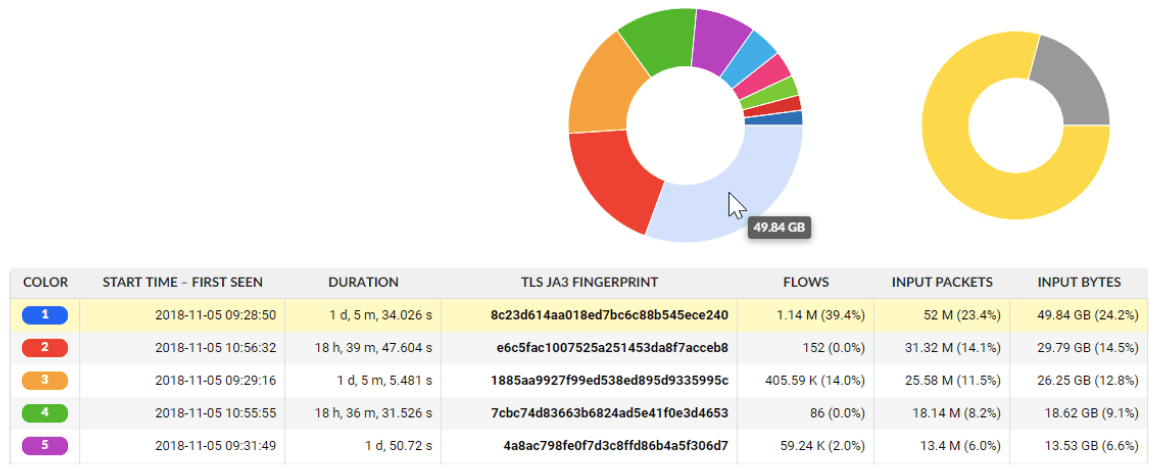
This method is very much in the field of signatures, and thus Flowmon utilizes reliable blacklists and whitelists. Beside others, it is an important part of encrypted traffic analytics which allows you to find outliers and other oddities in your network.


