Estimated reading time:3 minutes

The inability to access critical digital assets can have catastrophic consequences for your operations. With Flowmon, a leading network detection and response tool, you can cover visibility gaps, detect ransomware at an early stage and act before it harms your business.
Ransomware is one of the most common, and yet scariest, online assaults. It is a type of malicious attacker activity or a code designed to deny access to data and systems and demanding payments for restoring access to them.
Flowmon is a network detection and response tool utilizing an AI-powered engine combined with a number of advanced techniques to detect the footprints of an ongoing ransomware attack in its early stages. It helps to isolate the problem and respond before the ransomware starts spreading across your digital assets and impacts the business.
Early Ransomware Detection and Response
Due to the spread of BYOD, Internet of Things and cloud adoption, today’s infrastructure is evolving far beyond the perimeter, challenging end-point security tools to provide sufficient visibility. The ever-changing nature of ransomware oftentimes allows it to slip under the radar of the perimeter, bypass end-point security, and get lost in a bunch of false positives or hide in blind spots in network visibility.
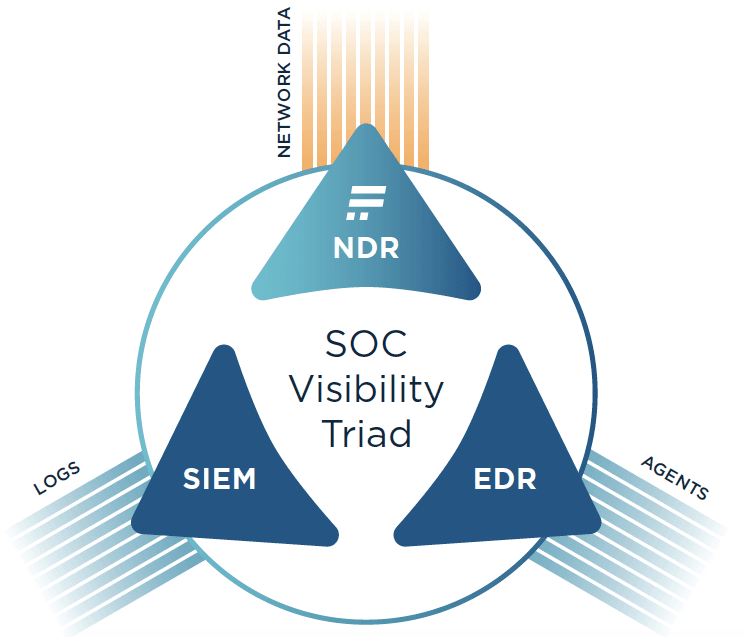
This is why security teams turn to a security model that extends log management and end-point protection with network detection and response tools. Known as the SOC visibility triad, this approach compensates for the weak points of its individual parts (EDR, NDR, SIEM) and gives full visibility across complex IT environments.
The SOC Visibility Triad is a concept created by Anton Chuvakin of Gartner, which postulates that deploying complementary security tools that make up for each other’s shortcomings will significantly reduce the chances that an attacker will be able to achieve their goals. The Triad consists of three pillars:
- EDR for endpoint security.
- SIEM for processing logs and correlating events.
- NDR for behavior analysis from the network perspective.
Continuous Visibility to Find Indicators of Compromise Quickly
Flowmon is one of the pillars of the SOC triad. It makes the entire incident management and response process more effective by supplying security experts with continuous visibility across networks while detecting anomalies and indicators that point at ransomware attacks. It alerts administrators on abnormal behavior in network traffic, giving them the ability to detect ransomware before digital assets suffer lockdown, investigate the incident, and trace the attackers’ footprints across the system.
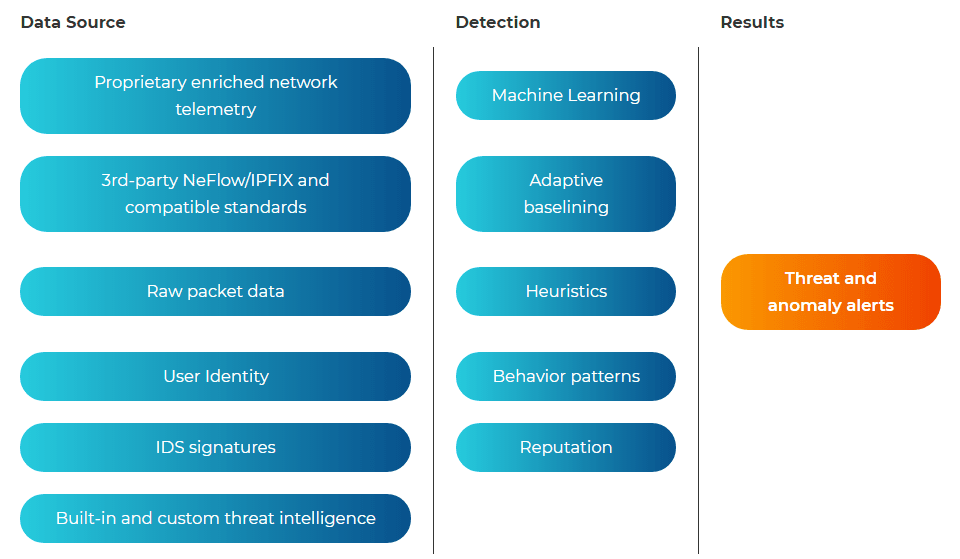
Flowmon does not use just one detection mechanism, but several, all working at the same time. They cover a wide number of scenarios by examining the network from several points of view. For instance, threats that would escape detection by reputation databases will be revealed by entropy modeling. Because the solution uses network traffic metadata for its analysis, it has no problem delivering the same level of detection accuracy in encrypted traffic as well.
With Flowmon, network experts can benefit from:
- Continuous monitoring of all networks across on-demand, datacenter, cloud, and hybrid infrastructure.
- A leading breach detection engine that detects atypical behavior that occurs in data streams using various methods, including machine learning, heuristics, behavior patterns, adaptive baselining, reputation databases, and signature-based detection.
- Automated response via integration with network access control or firewalls.
- East-west traffic visibility to cover gaps left by traditional approaches.


