Estimated reading time:4 minutes

Flowmon Anomaly Detection System from Kemp now contains Indicators of Compromise (IoC) for the SUNBURST trojan specifically. Users of the Flowmon network detection and response (NDR) tool can check if they are under attack and set up measures to detect SUNBURST.
This December, the world shook at the news of several US government bodies falling victim to a highly sophisticated attack. The breach was carried via what is known as the SUNBURST backdoor vulnerability, a trojanization of a legitimate security software update of the Solarwinds Orion platform.
What Is the SUNBURST Backdoor Attack?
SUNBURST is a very serious attack that creates a backdoor out of the network to an external server, allowing the attacker to instruct the infected machine what to do. Once it establishes a reverse communication channel from the compromised host to the attacker/control machine, it becomes difficult to block. See this analysis by FireEye for details.
SUNBURST Detection in Your Network
As a network detection and response tool, Flowmon tackles new and zero-day threats with a signatureless approach.
It uses the principles of behavioral analysis, which allow it to detect attacks without having any prior knowledge of them. With the help of machine learning, it detects network traffic (network communication) anomalies, such as lateral movement or data exfiltration, by default and can do this no matter the type of attack.
If an adversary does manage to breach the perimeter and start acting within the network, Flowmon will detect their movement as part of its standard functionality and thus buy you time to stop them.
The SUNBURST malware is able to map the hostnames within the victim’s environment and then set these hostnames on their command and control infrastructure to avoid suspicion. Fortunately for defenders, the attacker’s infrastructure leaks these hostnames in RDP SSL certificates. Flowmon is able to extract the information from SSL certificates and therefore you can query the Flowmon Monitoring Center to perform analysis of certificates that were used in communication between hosts in your network and public servers and look for a potential match with hostnames that are used in your environment.
For the SUNBURST malware, it is typical that the attacker chooses his IP addresses from countries where the victim is located. No matter which country is involved our behavioral analysis engine is able to detect data hoarding using the HIGHTRANSF method as well as data exfiltration using the UPLOAD method.
Indicators of Compromise
On top of the standard detection methods, Flowmon contains a set of Indicators of Compromise to detect SUNBURST specifically. Your Flowmon appliance will download them automatically (assuming it is connected to the Internet) and you may use them to prevent the infection or check whether it isn’t in your infrastructure already.
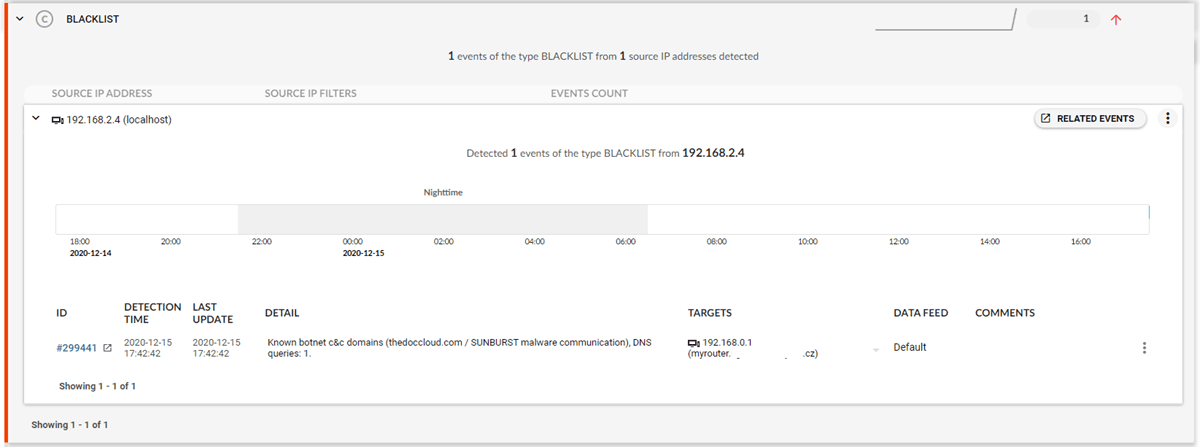
The attack is detected as a BLACKLIST event that alerts you to communication with a known botnet command and control center (see figure 1) while the detail of the event shows specific malware or botnet family that is attributed to the indicator of compromise. In this case SUNBURST.
What Else to Do
Unfortunately, the work does not end with detecting and removing the SUNBURST compromised host. You need to determine the scope of the breach as your network might be compromised, meaning that other hosts may have been infected.
Flowmon can be of great help as it can go back in time, analyze all the collected network telemetry, and reconstruct the activity on the network level. You can look for the indicators of compromise in historical traffic before they are known publicly. You can use Flowmon to understand the scope of the breach and identify other potentially compromised hosts.
Flowmon can be of great help as it can go back in time, analyze all the collected network telemetry, and reconstruct the activity on the network level. You can look for the indicators of compromise in historical traffic before they are known publicly. You can use Flowmon to understand the scope of the breach and identify other potentially compromised hosts.
Importance of NDR
No one is happy when things like SUNBURST happen. At present, we can only speculate about the origin of the threat.
However, it is yet another proof of the growing importance of NDR technologies as a mature partner to other signature-based detection tools.


