Estimated reading time:3 minutes
The vulnerability called SIGRed (CVE-2020-1350) has been around for 17 years, during which time it was present in Windows Server operating systems from version 2003 through 2019 and received a maximum severity rating of 10. It was finally patched in July 2020.
As the vulnerability allows an attacker to perform remote code execution on Windows Server via DNS, it poses an extremely serious danger and can propagate over the network without user interaction. As Windows Server typically acts as the domain controller as well, exploiting it over the network allows the attacker access to company crown jewels without obstacles.
The first public SIGRed proof of concept exploit has recently been published by Grapl lead security researcher Valentina Palmiotti. Flowmon ADS has been able to detect the exploitation of this vulnerability since August 2020, so effectively more than 6 months before the exploit had appeared.
Behavior patterns
The detection is based on a unique Flowmon technique called “behavior patterns” that describes malicious behaviors using network telemetry data instead of packet-level signatures. In contrast to traditional signatures, behavior patterns are resistant to traffic encryption and more capable of dealing with payload modifications, as the payload is not the primary focus of any particular detection method.
After the exploit was published, we tested the ability of Flowmon ADS to detect the exploitation of SIGRed vulnerability and successfully demonstrated that the detection technique designed months prior to the availability of this particular exploit is able to recognize the malicious behavior in the network traffic without any need for modification. This implies that algorithms leveraged by Flowmon ADS are ready to detect unknown threats and zero-day attacks.
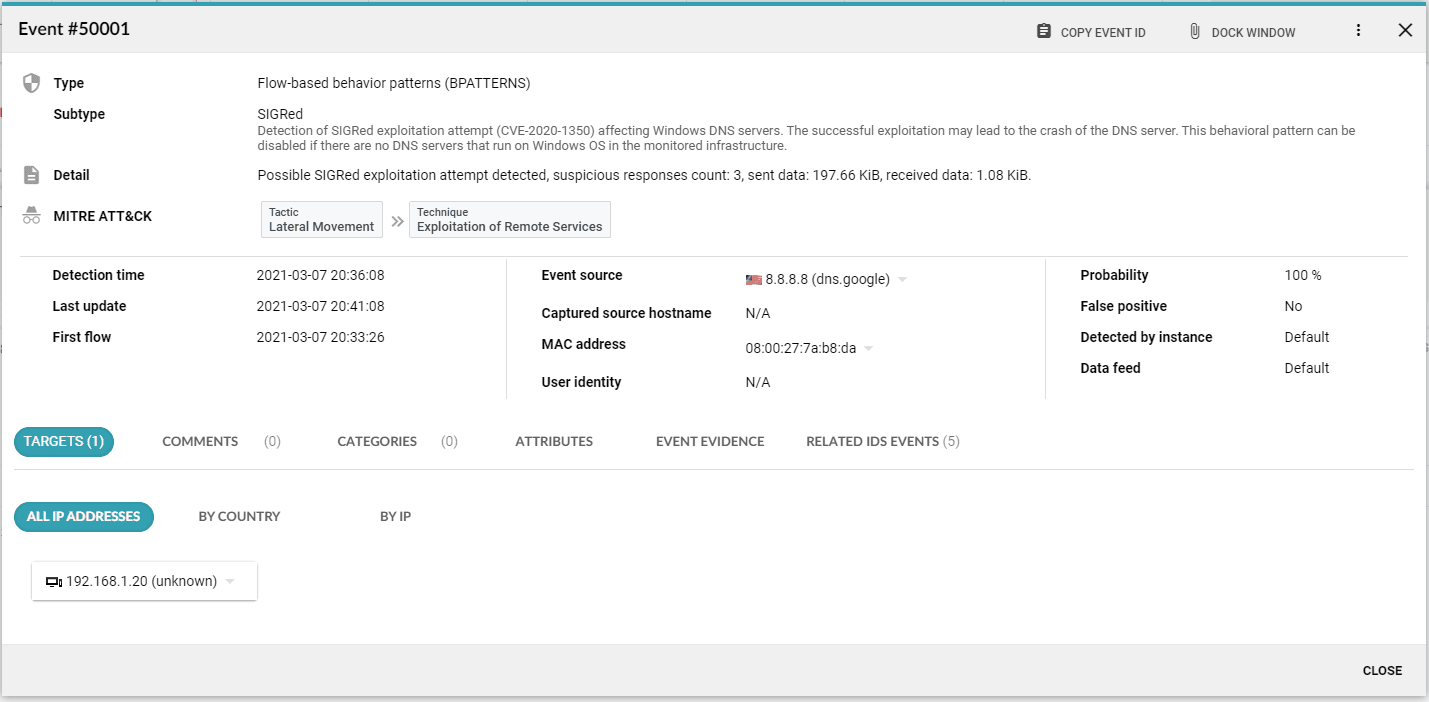
Vulnerabilities like SIGRed appear every day. NDR (Network Detection and Response) is a fast-advancing technology that can help you to detect malicious behavior in a timely manner even when the signature of that particular attack is not available yet. When combined with proper network telemetry collection, storage, and analysis you can match your network traffic against known indicators of compromise or leverage network telemetry for threat hunting.


