Estimated reading time:4 minutes
Common Goals, One Tool, Streamlined Operations.
Even though they pursue different priorities, NetOps and SecOps share the same goal – ensuring healthy and efficient business services. Forward-thinking leaders know how to break the walls that stand between the two teams and bring out the value they can offer each other, making operations more agile, less risky and more cost-effective. Flowmon is a shared NetOps and SecOps tool that fosters this cooperation.
Allow Teams to Speak the Same Language
The traditional view is that NetOps and SecOps are independent silos with different technologies and processes. But in the event of data leakage, outage or performance degradation, it doesn’t matter what the root cause is. What matters is resolving the incident as quickly and efficiently as possible so that business isn’t harmed.
When NetOps and SecOps teams share a dataset and toolset, they gain the ability to make joint decisions and construct efficient security policies that do not affect performance. Moreover, coordination on tool spending and focus on shared data, use cases and technologies brings significant savings on purchase, support, training and staff overhead.
Benefits
- Optimizing spending: Merged procurement avoids purchasing multiple technologies with overlapping functionality and improves cost-efficiency in support, staff training and overhead.
- Risk reduction: The ability to enforce compliance policies, oversee unwanted behavior and evaluate data accesses in real time helps eliminate risk.
- Breach impact minimization: Efficient cooperation on incident investigation and handling reduces response time to contain the threat in its early stages.
- One source of truth: The ability of both teams to access the same information via a shared platform enables them to piece together meaningful context and make decisions.
- Fast time to value: Streamlined deployment, user enablement, predefined views, dashboards and reports. From deployment to data on the dashboard in just 30 minutes.
Infrastructure Design & Deployment
Infrastructure needs to be built with both performance and security in mind. While the NetOps team will appreciate Flowmon’s data on network structure during sizing, capacity planning or performance management, SecOps teams will use the same data to identify non-approved service traffic. This comes in handy e.g. when configuring a new firewall, where new blocking policies can be tested in real time and readjusted as necessary, saving time and effort in deploying the new firewall.
Incident Monitoring & Investigation
Perimeter and endpoint security can only protect against threats of known signature. The rest require a layered security model that can monitor the gap between perimeter and endpoint and pick up indicators of compromise on the network level. While some do not necessarily pose a security risk and can be disregarded by the SecOps team, they could be an anomaly that the NetOps team picks up and engages with security to act before the breach becomes serious. This includes identifying parts of the network that were compromised, assets and users affected, and what needs to be re-installed or recovered. This information is extracted from network metadata and presented to both NetOps and SecOps to decide on the next steps together.
Incident Response
When it comes to response, it is the SecOps team who assesses the risk and decides how to mitigate, but it’s the NetOps team who carries it out on the network level, using Network Access Control, DHCP, SDN controllers, firewall or other techniques. Coordination between the teams and agreement on the remedial action is essential for faster time-to-respond. Flowmon can automatically trigger an action via integration with 3rd party tools that can be used for incident response. For instance, it can connect to Cisco ISE through pxGrid and quarantine a malicious IP address.
Policy Verification and Enforcement
Flowmon collects rich network traffic metadata and provides visibility even into encrypted sessions between clients and servers. These are available regardless of the client’s physical location or whether the server runs in the cloud or datacenter. This provides a wealth of insight about the traffic and allows identification of communication partners, services, applications and even data such as out-of-date SSL certificates, policy non-compliant certificates, encryption strength and old TLS versions that may contain faults or vulnerabilities. Flowmon further stores full communication statistics for weeks or even months and auto-triggers the recording of detected anomalies to provide full packet trace of the event.
Network Traffic Analysis for NetSecOps
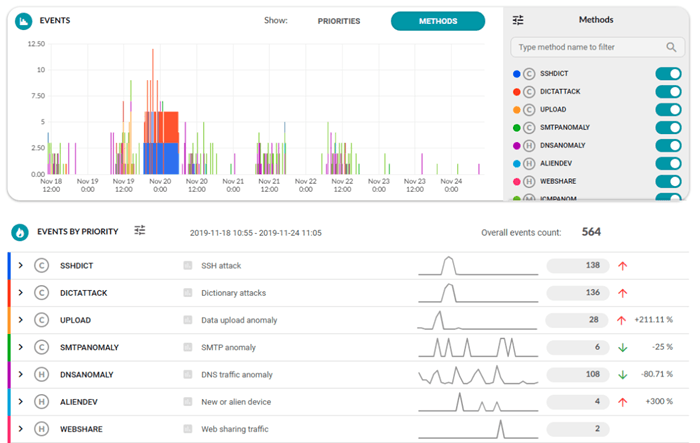
Flowmon collects network telemetry data from a variety of sources including your existing network devices and its own sensors, in which case the process is passive and doesn’t interfere with the network’s performance. The data is then processed using machine learning, heuristics and advanced algorithms. Relevant information is extracted and visualized on the dashboard.
While NetOps teams benefit from insight into network traffic, which is essential for their ability to manage application performance and resolve emerging issues, SecOps layer their security strategy to detect unknown and insider threats (even in encrypted traffic). Together, they use shared data to make decisions on infrastructure design, enforce security policies across the entire IT ecosystem, investigate, assess impact and respond to threats and data breaches. Thanks to Flowmon, informed decision-making and prioritization are always supported by reliable intelligence.


