Estimated reading time:6 minutes
In total, researchers said they found more than 6,800 hidden backdoor/function apps on the Play Store, more than 1,000 on third-party stores, and almost 4,800 pre-installed apps on devices.
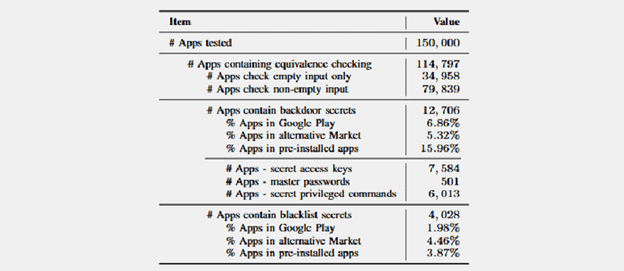
A detailed academic analysis released this week has found some hidden backdoor-style actions – such as secret access keys, master passwords, and secret commands – in over 12,700 Android applications. Android Software contains master passwords, secret access keys, and hidden commands.
Academics in Europe and the United States have developed a specialized method called InputScope to investigate this secret activity, using which they can analyze input type fields contained within 150,000 Android applications.
More specifically, academics evaluated the top 100,000 play store applications, the high 20,000 applications hosted in third-parties app stores, and over 30,000 devices pre-installed on Samsung handsets.
“Our evaluation uncovered a concerning situation,” the research team said. “We identified 12,706 apps containing a variety of backdoors such as secret access keys, master passwords, and secret commands.”
Investigators claim these secret backdoor mechanisms can allow attackers to access users ‘accounts unauthorized. Also, the attacker with physical access to a computer may give attackers access to a phone or allow them to run code in elevated privilege devices (because of the hidden secret commands that are contained in the input fields of the applications), if any of these applications is enabled.
Some samples of hidden “backdoor” type
Referring to one particular example, the research team said,“By manually examining several mobile apps, we found that a popular remote control app (10 million installs) contains a master password that can unlock access even when locked remotely by the phone owner when [the] device is lost,”
Meanwhile, we also discovered a popular screen locker app (5 million installs) uses an access key to reset arbitrary users’ passwords to unlock the screen and enter the system.
In addition, we also found that a live streaming app (5 million installs) contains an access key to enter its administrator interface, through which an attacker can reconfigure the app and unlock additional functionality.
Finally, we found a popular translation app (1 million installs) contains a secret key to bypass the payment for advanced services such as removing the advertisements displayed in the app.
As the research team reveals, some problems present a direct danger to the user’s safety and the data stored on the device. In contrast, other issues were only harmless Easter eggs or testing features that unintentionally put it into production.
The research team told all device developers of secret conduct or a backdoor-like process. But not all app devs have responded.
As a consequence some apps presented in the white paper of the team have had their names written to protect their users.
Additional research information is provided by scientists from Ohio State University, New York University, and the CISPA Helmholtz Center for Information Security, published in “Automatic Uncovering of Hidden Behaviors FromInput Validation in Mobile Apps,”
Since the InputScore tool analyzed input fields in Android applications, the academic team also found that applications use secret bad word filters or politically motivated blacklists. In total, researchers have identified 4,028 Android apps with blacklists of inputs.
Warning of malicious Android apps
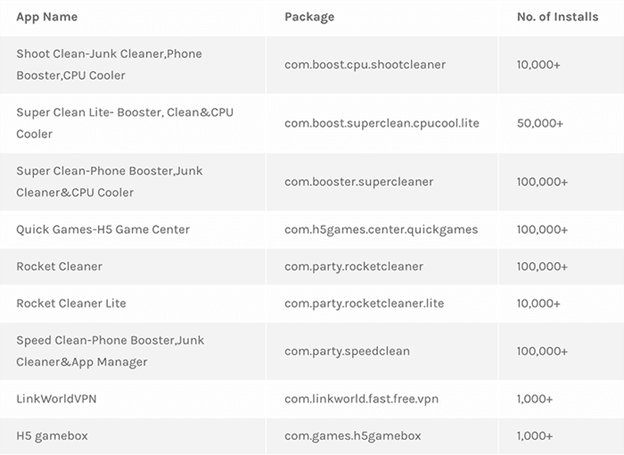
In February, Gizchina.com revealed nine malicious Android apps from the Play Store that were downloaded 470,000 times masquerading as performance optimization tools.
In fact, these apps gained unauthorized access to users' Google and Facebook accounts. This is what Trend Micro, a Japanese company specializing in cybersecurity, revealed.
Accordingly, Trend Micro posted a report of malware targeting Android users from the Play Store.
The strategy employed here is quite dangerous. Malware actually hides in apps with names like “Speed Clean” or “Super Clean”.
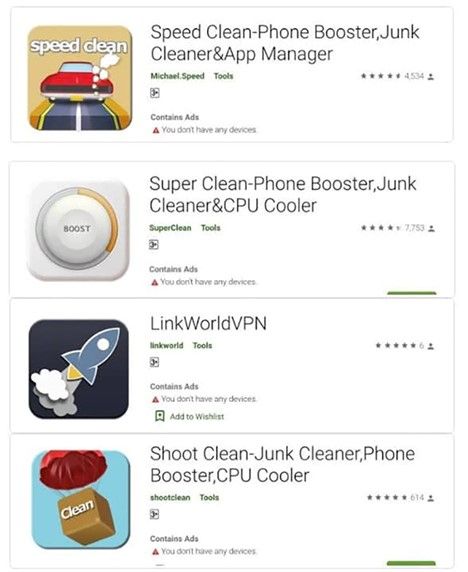
In other words, hackers have used the idea of impersonating applications to speed up the phone to trick users into downloading, because in terms of operating mechanism, these apps are essentially performance optimization tools for your phone.
Instead of performing normal operations, these apps will automatically download 3,000 more malicious files, and as a result, the app can gain unauthorized access to the user's Google and Facebook accounts to conduct fraudulent advertising.
These cleaning tools, along with others, will run ads from legitimate platforms like Google AdMod or Facebook Audience Network, and then automatically execute clicks on ads for profit.
These fake apps also prompt the user to grant them permission while disabling Play Protect, the security program in the Google Play store. This allows more and more phishing software to be downloaded undetected.
Finally, they can also use accessibility options to post fake reviews and ratings to Google Play to lure others to download.
The affected apps have now been removed from the Play Store by Google, but it is expected that the malware will continue to attack with other fake apps. The countries most affected are Japan, Taiwan, the United States, Thailand and India.
Detecting malicious applications on Android phones will help you distinguish between safe applications and malicious applications, thereby minimizing the download of dangerous applications and protecting your privacy. Make your Android device more secure.
According to security experts, users need to use the malicious application detection feature, Scan for harmful applications on Android, do not install applications of unknown origin, always update the Android version, limit the level Excessive device permissions to prevent malicious apps from collecting and using personal data.

